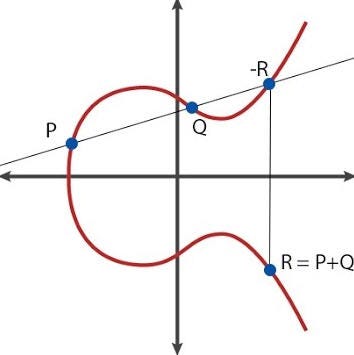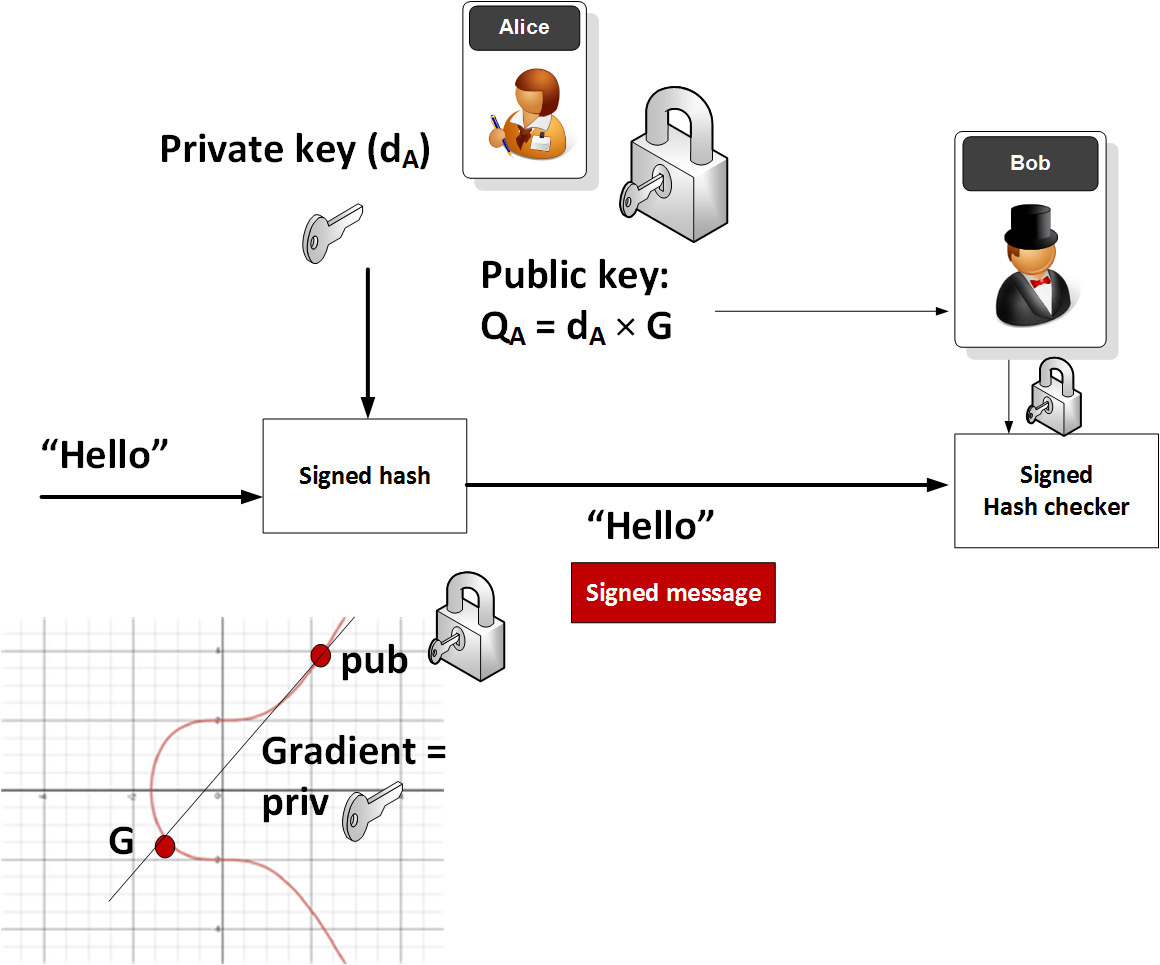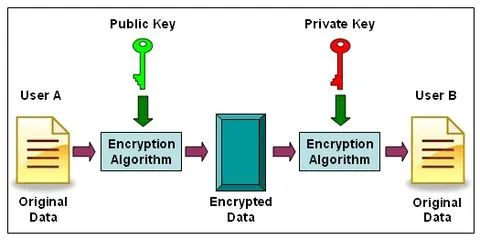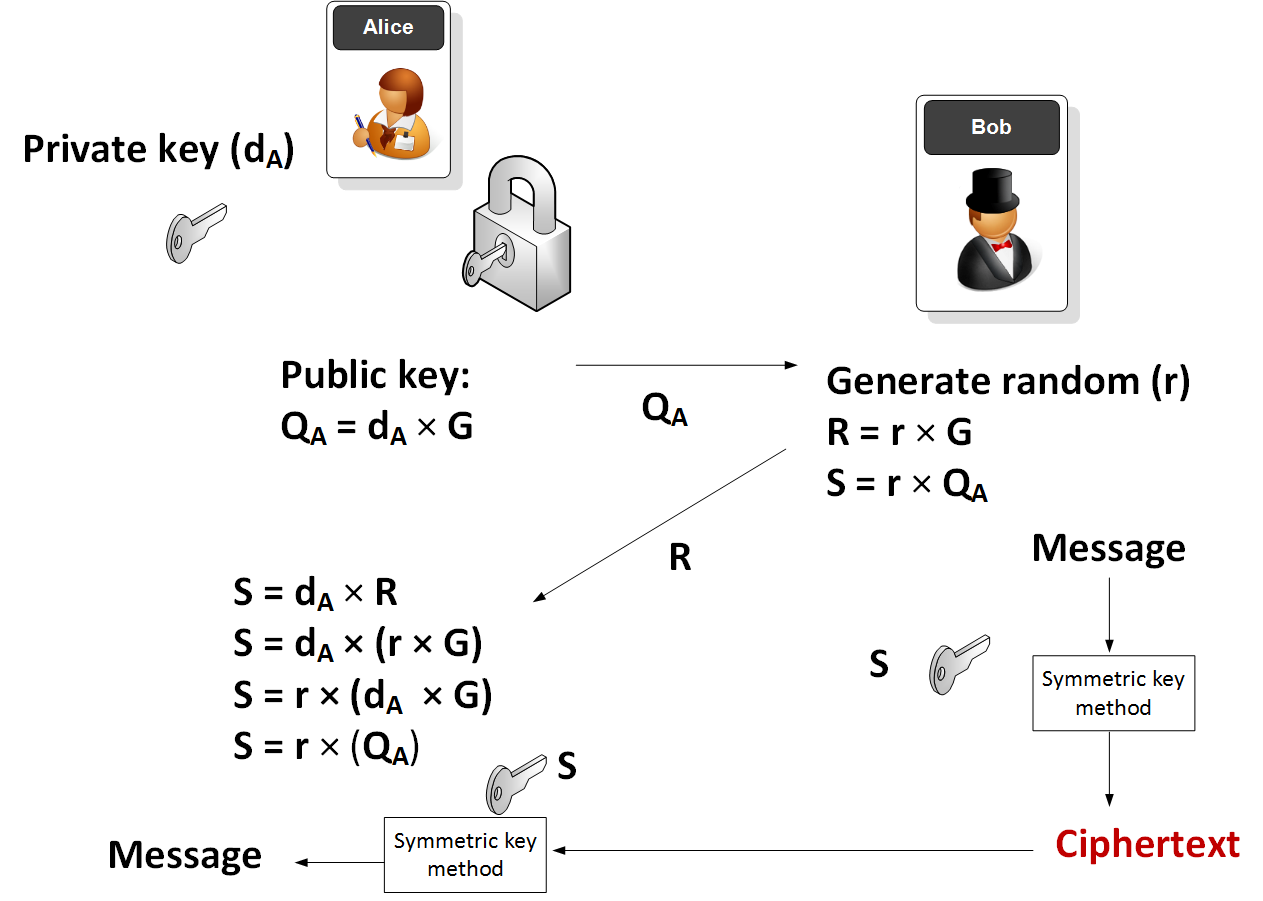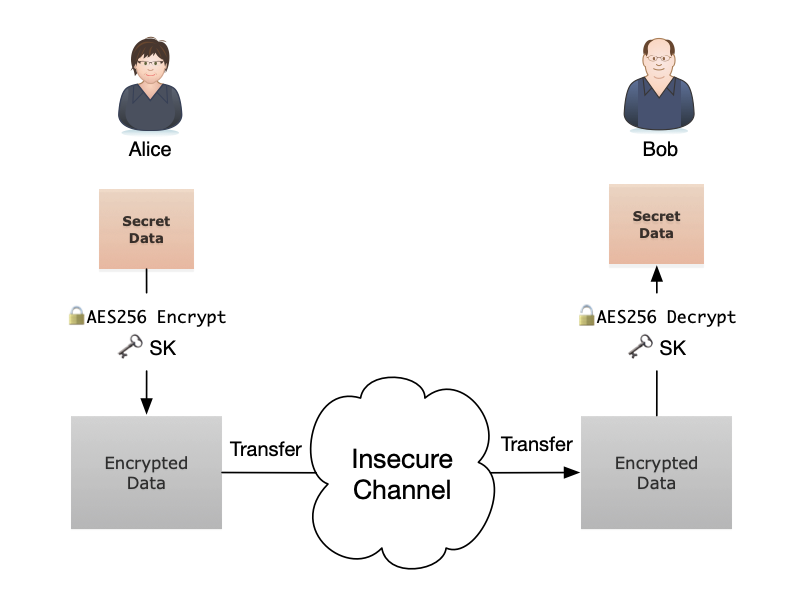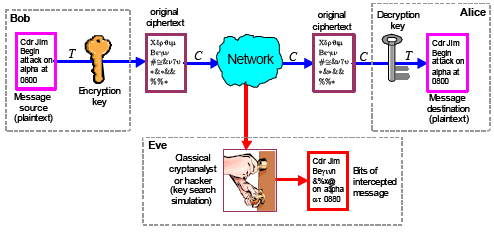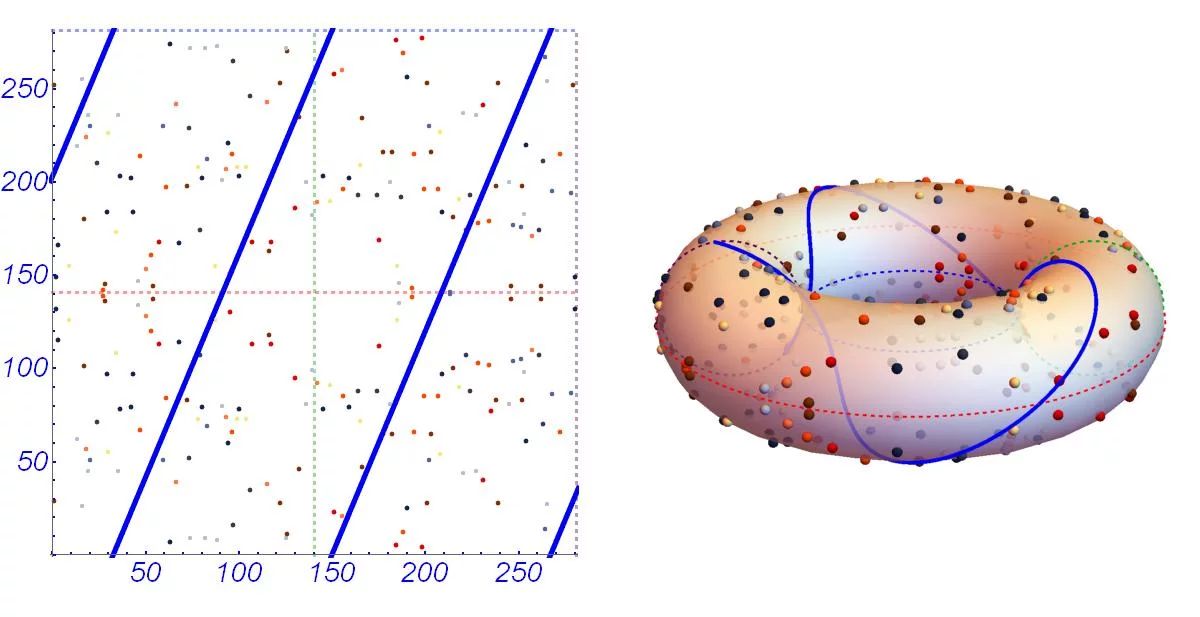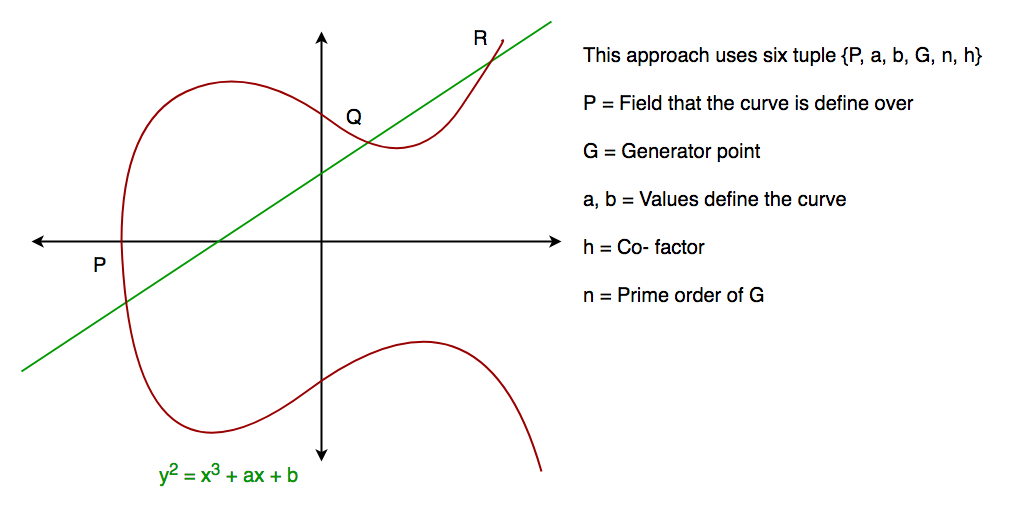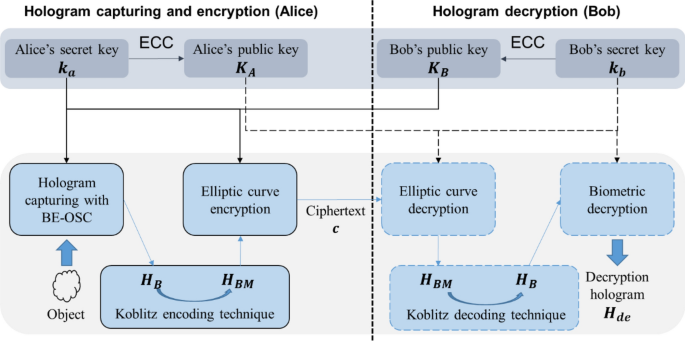
Asymmetric cryptosystem based on optical scanning cryptography and elliptic curve algorithm | Scientific Reports
The proposed OSS digital signature flowchart based on elliptic curve... | Download Scientific Diagram
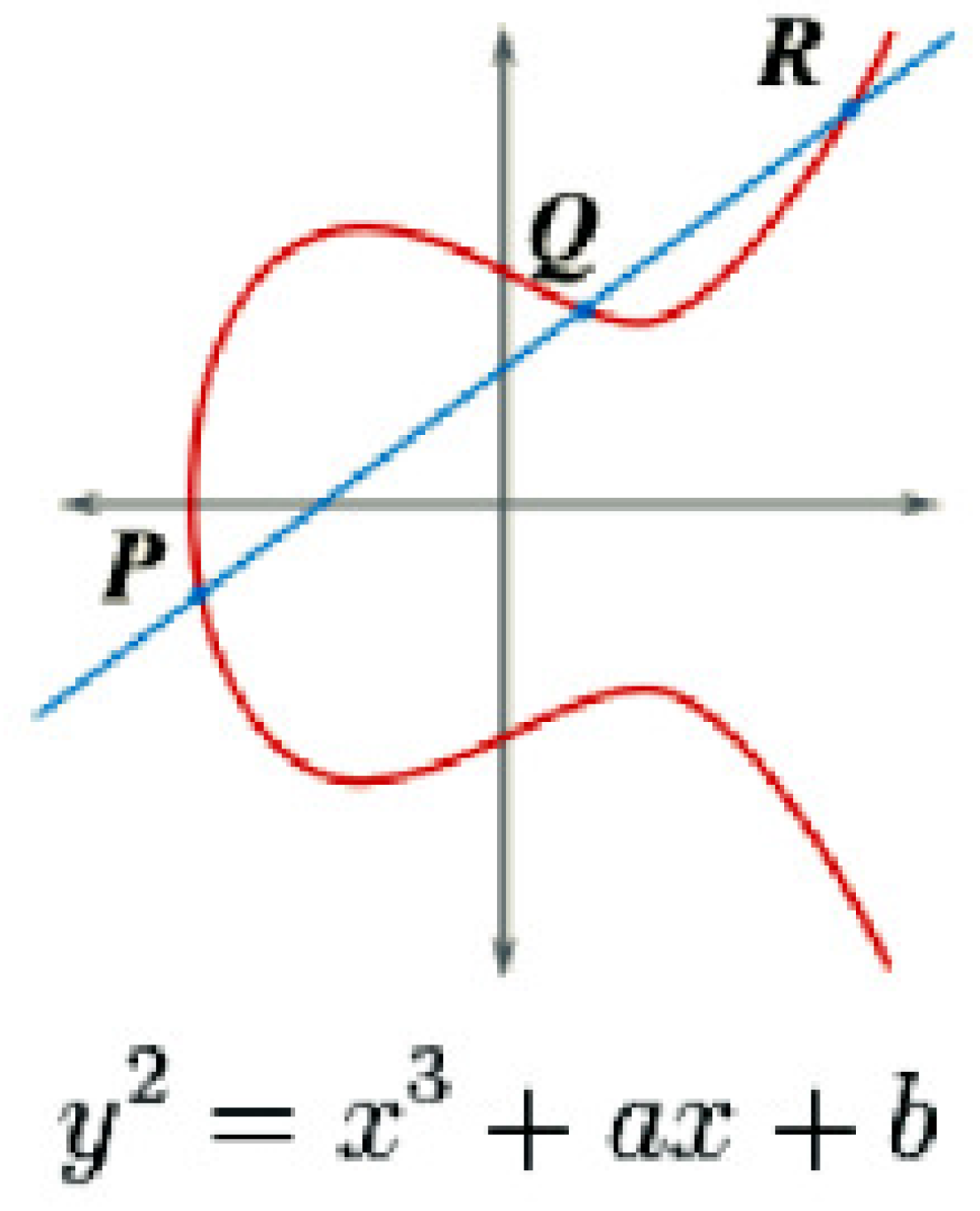
Cryptography | Free Full-Text | Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols